


For decades, the Linux kernel has been an ecosystem rooted in C a language close to the metal, fast, and widely understood by systems programmers. However, with evolving hardware complexity, increasingly sophisticated attacks, and an ever-growing demand for memory safety, C is beginning to show its age. Enter Rust, a modern systems programming language designed with safety and performance in mind. In this blog, we explore how the rust linux kernel initiative is revolutionizing kernel-space development by introducing safer abstractions without compromising low-level control.
This post dives deep into the technical integration of rust linux kernel, real-world use cases, architectural patterns, the state of driver support, compile toolchains, and a roadmap for kernel contributors. We also address criticisms, provide technical examples, explore testing methodologies, and examine the socio-technical impact of bringing Rust into kernel-space. Let’s dissect why rust linux kernel is now a first-class citizen in the most mission-critical layer of open-source computing, and what lies ahead for its evolution.
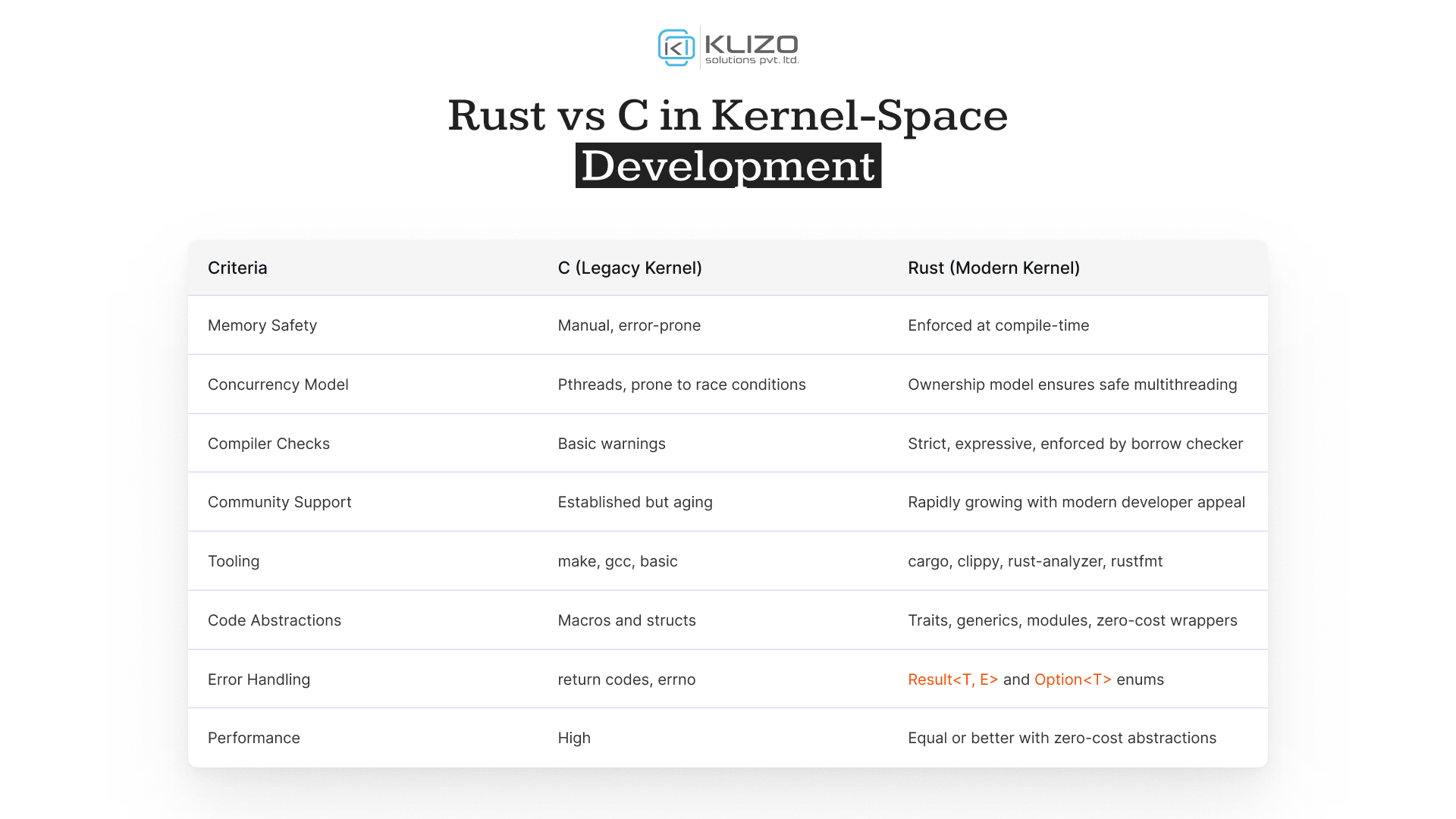
C is powerful but comes with no built-in memory safety. Common bugs like buffer overflows, use-after-free, double frees, integer overflows, and race conditions have plagued the kernel since its inception. These bugs not only destabilize systems but often become severe security vulnerabilities exploited by attackers.
Linux kernel maintainers deal with hundreds of CVEs annually. A large proportion of these stem from memory issues, especially when handling user-space input, device buffers, or multi-threaded access. Even expert kernel developers can struggle with safe memory handling in C. The consequences? Kernel panics, privilege escalation, and complete system compromise.
Rust’s ownership model statically enforces memory safety at compile time. It removes entire classes of errors, such as:
Rust achieves this through:
Option and Result)Unlike other safe languages, Rust offers zero-cost abstractions: performance similar to C but with safer constructs. This makes it ideal for writing low-level components like drivers, allocators, filesystems, schedulers, and IPC mechanisms inside the rust linux kernel.
Major organizations like Google, Microsoft, AWS, Red Hat, Meta, and the Internet Security Research Group (ISRG) are actively investing in rust linux kernel initiatives. Notably:
Rust’s emergence has also rejuvenated community interest in contributing to kernel development. Younger developers, who find C intimidating, are more inclined to write safe, auditable code in Rust.
The Linux kernel community has debated memory-safe alternatives since the 2000s. D projects, Cyclone, and even SPARK Ada were considered. But only Rust combined performance with modern language ergonomics.
In 2020, Miguel Ojeda proposed Rust integration with a clean interoperability layer. The goal was not to rewrite Linux in Rust, but to augment existing C infrastructure, allowing for modular adoption.
Linux Kernel 6.1 (Dec 2022) merged foundational Rust support. It added:
This was hailed as a milestone, finally breaking the monopoly of C in kernel space.
Linux 6.3 through 6.8 introduced experimental and semi-stable drivers in Rust:
rnull: Null block driverExpect Linux 6.10+ to expand the roster with stable Rust drivers from multiple vendors.
To enable Rust support:
make menuconfig
-> General Setup
-> Enable Rust support (CONFIG_RUST=y)You also need a compatible toolchain:
rustup, cargorust-bindgenThe rust linux kernel build system uses Kbuild extensions to recognize .rs files, compile them with rustc, and link object files with traditional C modules.
Rust kernel modules follow a trait-based interface. A minimal module looks like:
use kernel::prelude::*;
module! {
type: MyModule,
name: b"rust_sample",
author: b"klizos.com",
description: b"Sample rust linux kernel module",
license: b"GPL",
}
struct MyModule;
impl KernelModule for MyModule {
fn init() -> Result<Self> {
pr_info!("Rust module initialized\n");
Ok(MyModule)
}
}Rust modules are reference-counted and destructors (Drop) are called when unloaded-automatically freeing memory.
Rust can call C functions and vice versa using FFI. Kernel developers can expose C headers via bindgen! macros or manually write bindings. Safety must be validated at the Rust boundary.
Low-level operations (e.g., pointer math, DMA) still require unsafe blocks, but are localized and auditable. Common crates include:
kernelcoreallocvtablePinning ensures immovable memory for objects registered with subsystems (like /proc or /sys entries).
Drop-in block driver used for benchmarking and testing block subsystems.
Part of mainline Linux PHY layer using safe Rust wrappers over MDIO.
Experimental in-kernel Rust implementation for ultra-fast NVMe networking layers.
Google’s implementation of IPC in Android kernel now supports Rust components.
Asahi Linux writes DRM drivers in Rust for Apple silicon-highlighting real-world graphics performance.
Rust-based tarball filesystem driver for educational and sandbox use cases.
Rust brings composability to the rust linux kernel through trait-based APIs, generic types, and advanced pattern matching.
Interfaces such as FileOperations, BlockDriver, and NetDevice are defined as Rust traits. They enforce method contracts, allow mocking for tests, and promote extensibility.
Rust enums like Result and Option replace legacy status codes and NULL pointers with strict, checked flows.
Using Arc, Mutex, and SpinLock, developers can write thread-safe code without data races. Rust ensures these constructs are used within the right ownership scope.
No more return -EINVAL. Instead:
fn read(&self) -> Result<usize> {
Ok(self.buf.len())
}This makes intent explicit, encourages error bubbling, and reduces surprises.
rustup install nightly
rustup default nightlyMake sure cargo and clang are installed. The rust-analyzer language server helps during development.
#[cfg(test)]make LLVM=1 CIclippy for lintingrustfmt for code formattingcargo-bloat and cargo-llvm-lines for binary size inspection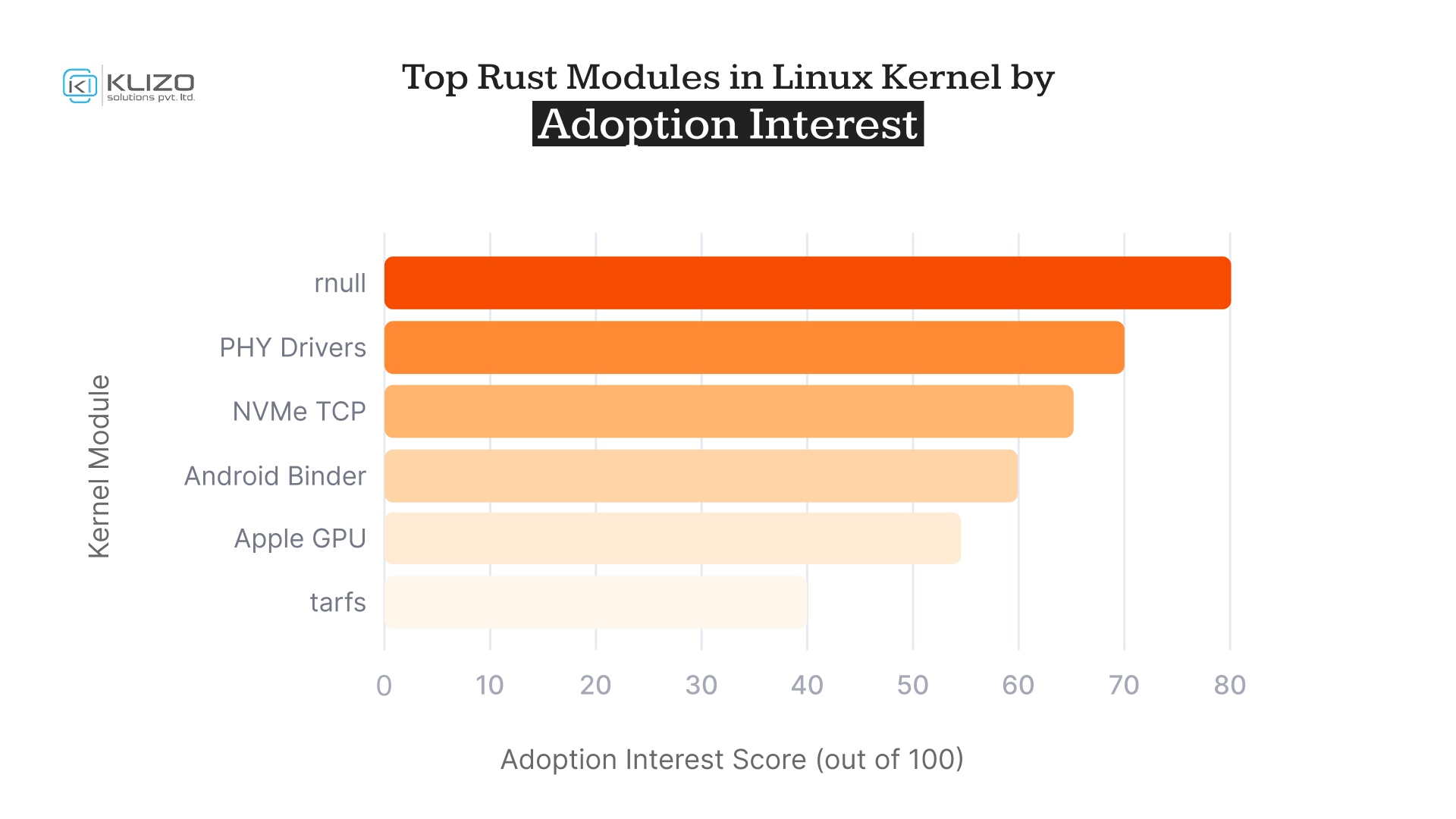
Still, for memory-critical subsystems, the rust linux kernel offers better long-term viability.
Security researchers estimate a 30–50% drop in kernel CVEs over 5 years with Rust adoption. This transforms IoT, mobile, automotive, and embedded markets.
git clone https://github.com/Rust-for-Linux/linux.gitmake LLVM=1 allmodconfig
make LLVM=1Use samples under samples/rust/hello_world.rs as starting point.
rust-for-linux@vger.kernel.org#rust-for-linux:matrix.orgUse git send-email or b4 tooling to format patches for LKML. Follow the standard kernel contribution guidelines.
The rust linux kernel is more than an experiment – it’s a tectonic shift. It modernizes systems programming while preserving everything that made Linux robust. With vendor adoption accelerating, contributors rising, and code quality improving, this is the future of safe systems engineering.
Whether you’re a kernel veteran or a Rustacean, there’s a place for you in this new hybrid world. Embrace the learning curve, build responsibly, and help shape the next era of Linux development.
Joey Ricard
Klizo Solutions was founded by Joseph Ricard, a serial entrepreneur from America who has spent over ten years working in India, developing innovative tech solutions, building good teams, and admirable processes. And today, he has a team of over 50 super-talented people with him and various high-level technologies developed in multiple frameworks to his credit.

Subscribe to our newsletter to get the latest tech updates.