

| What You Learn | Key Takeaway |
|---|---|
| PQC Fundamentals | PQC algorithms (Kyber, Dilithium, SPHINCS+) are designed to resist quantum attacks. |
| PQC Integration | Integrating PQC requires careful planning, from hybrid encryption to full adoption. |
| Deployment Strategy | Start with hybrid encryption, migrate to dual-cert systems, then full PQC. |
| Use Cases | PQC secures sensitive data in healthcare, finance, and government sectors. |
Today’s cryptography relies on algorithms like RSA and ECC, which are difficult for classical computers to crack. However, quantum computers could break these in seconds using algorithms like Shor’s.
Post-Quantum Cryptography (PQC) introduces quantum-resistant algorithms to protect data now and in the future.
This article explores:
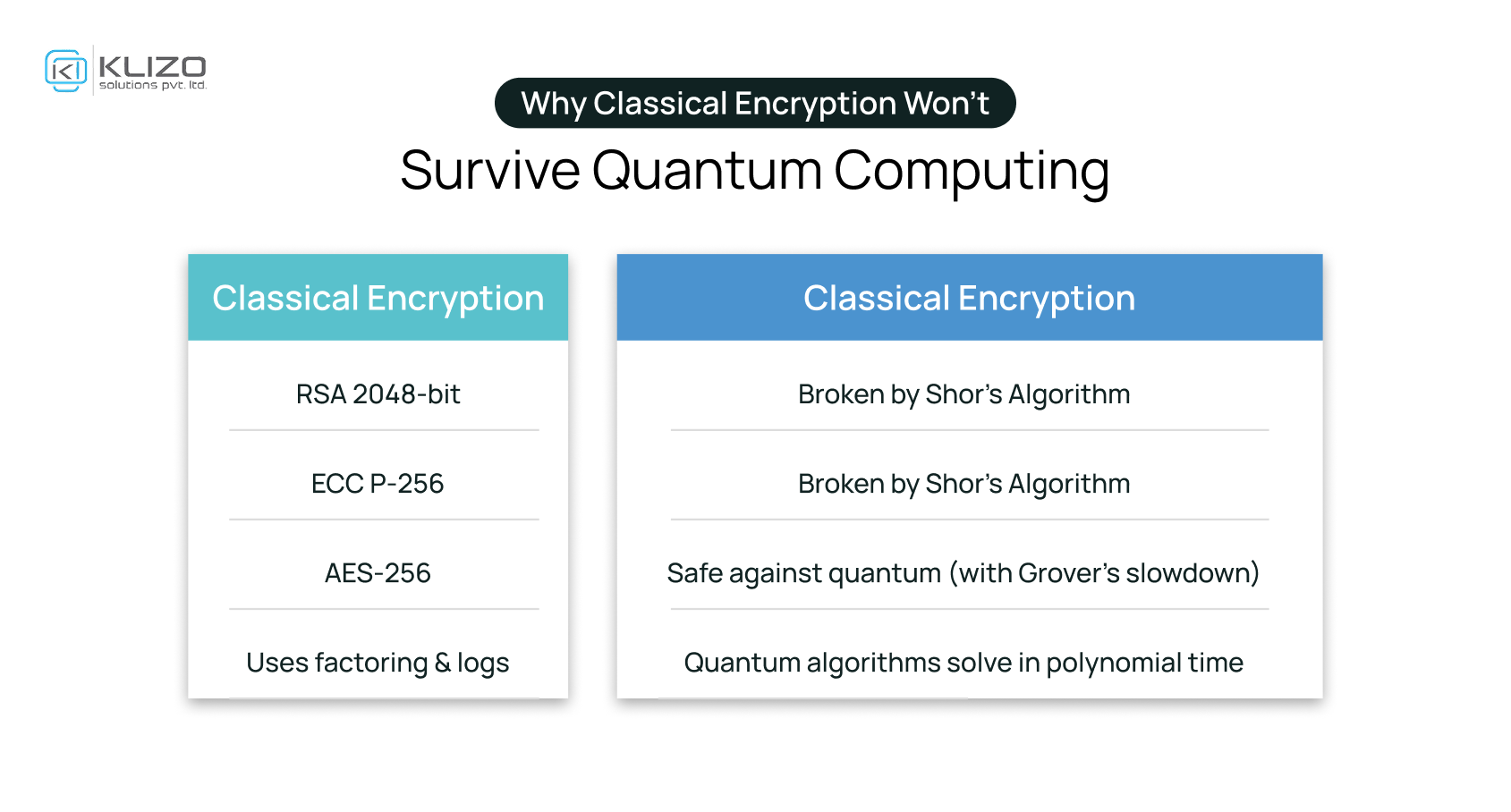
Post-Quantum Cryptography uses:
These algorithms are resistant to quantum attacks, ensuring long-term data security.
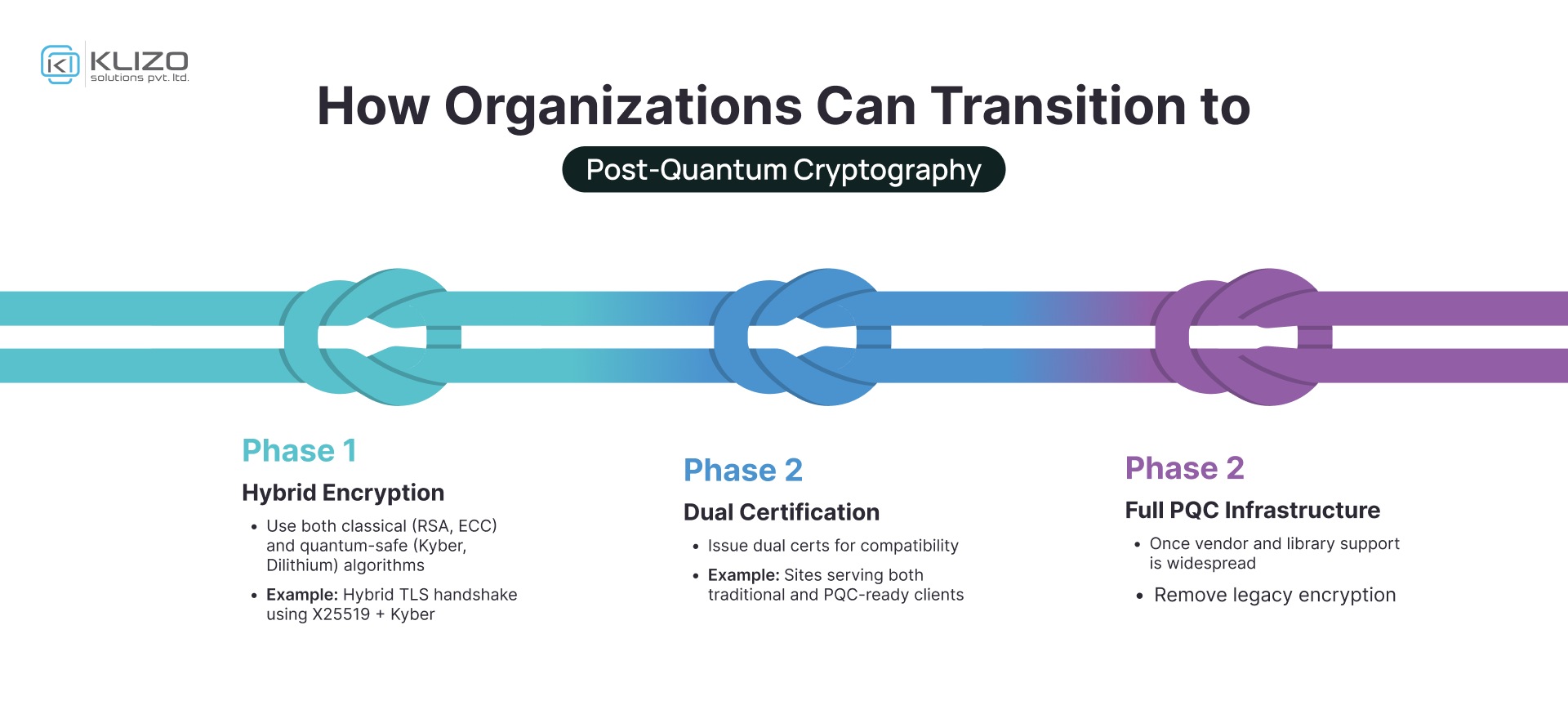
Combine traditional + quantum-safe algorithms (e.g., X25519 + Kyber) for compatibility and future safety.
Issue both traditional and post-quantum certs for gradual infrastructure migration.
Transition entirely to post-quantum once standards and support mature.
Performance and security policy changes must be factored into the implementation.
Use Kyber and Dilithium in hybrid TLS handshakes for secure and future-proof payments.
If your platform handles customer data, payment transactions, or intellectual property, integrating PQC isn’t optional—it’s inevitable. Modern SaaS teams must prioritize security engineering that evolves with computing power.
Key questions to ask:
By treating PQC as a proactive investment instead of a reactive patch, organizations can build long-term trust and future-proof their core architecture.
Quantum computing is no longer speculative—it’s accelerating. As data lives longer and attackers grow smarter, Post-Quantum Cryptography becomes a business-critical priority.
Organizations that begin PQC adoption today won’t just stay ahead of threats—they’ll be the ones setting tomorrow’s security standards.
The path forward:
PQC isn’t a finish line—it’s a mindset shift toward resilience.
Ready to get started? Contact Klizos for a PQC readiness workshop tailored to your tech stack.
Post-Quantum Cryptography refers to cryptographic algorithms that are secure against the power of quantum computers. You should care because quantum computers can break traditional encryption methods, which may expose your systems to future attacks even on data encrypted today.
Traditional encryption (RSA, ECC) relies on mathematical problems that classical computers find difficult. Quantum computers can solve these problems efficiently. PQC is designed to resist such quantum attacks using different mathematical principles like lattice-based or hash-based cryptography.
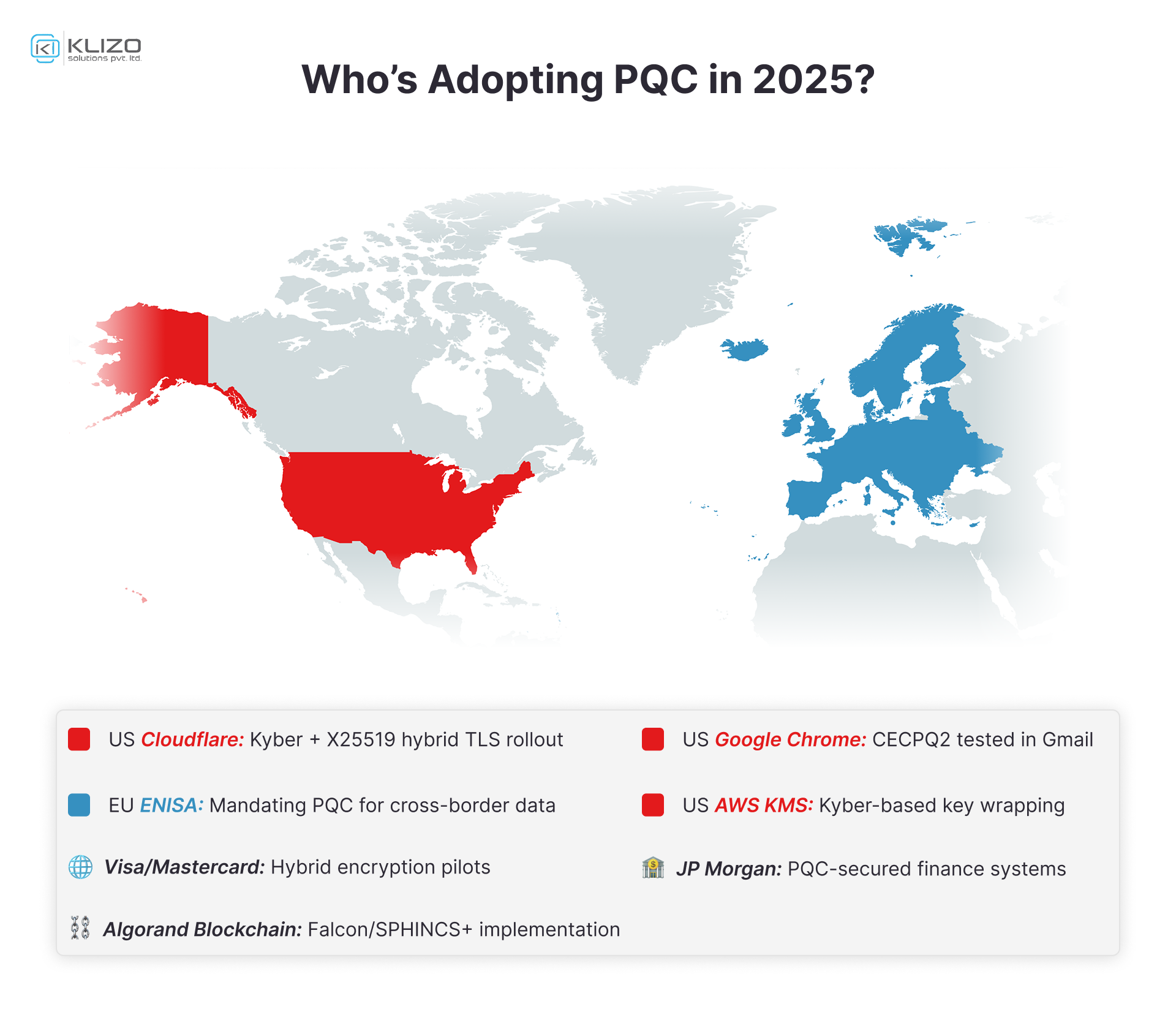
Yes. Libraries like OpenSSL, Bouncy Castle, and frameworks like OpenJDK 22 have started incorporating support for algorithms like Kyber and Dilithium. Adoption is growing rapidly.
Start with hybrid encryption—combine traditional algorithms with PQC in TLS handshakes. Follow a phased approach: Hybrid → Dual-Cert → Full PQC. Update your SDKs, dependencies, and security policies accordingly.
It depends. Some PQC algorithms use larger keys and require more computation. However, advances in optimization, hardware acceleration, and parallel processing are helping mitigate performance issues.
Industries like healthcare, finance, government, and blockchain use PQC to secure sensitive data, payments, and long-lived records. SaaS platforms handling customer data or IP should start planning their transition now.
Train your engineering and compliance teams. Monitor NIST standards. Use cryptographic libraries with PQC support. Partner with experts like Klizos to assess readiness and define your migration roadmap.
Joey Ricard
Klizo Solutions was founded by Joseph Ricard, a serial entrepreneur from America who has spent over ten years working in India, developing innovative tech solutions, building good teams, and admirable processes. And today, he has a team of over 50 super-talented people with him and various high-level technologies developed in multiple frameworks to his credit.

Subscribe to our newsletter to get the latest tech updates.