


In the vast ocean of digital content, truth and deception often swim side by side.
And Deepfakes, the uncanny digital doppelgängers, are increasingly blurring the line between reality and fabrication!
Yes, in an age where “seeing is no longer believing”, the rise of deepfakes—highly realistic and often deceptive AI-generated media—poses significant challenges for individuals and organizations alike.
From manipulated political speeches to AI-generated celebrity scandals, the threat is real, making deepfake detection more crucial than ever!
Wondering how to identify deepfake videos? Well, fear not!
In this article, we’ll equip you with all the possible ways to navigate this treacherous sea of misinformation and unmask the deepfake menace.
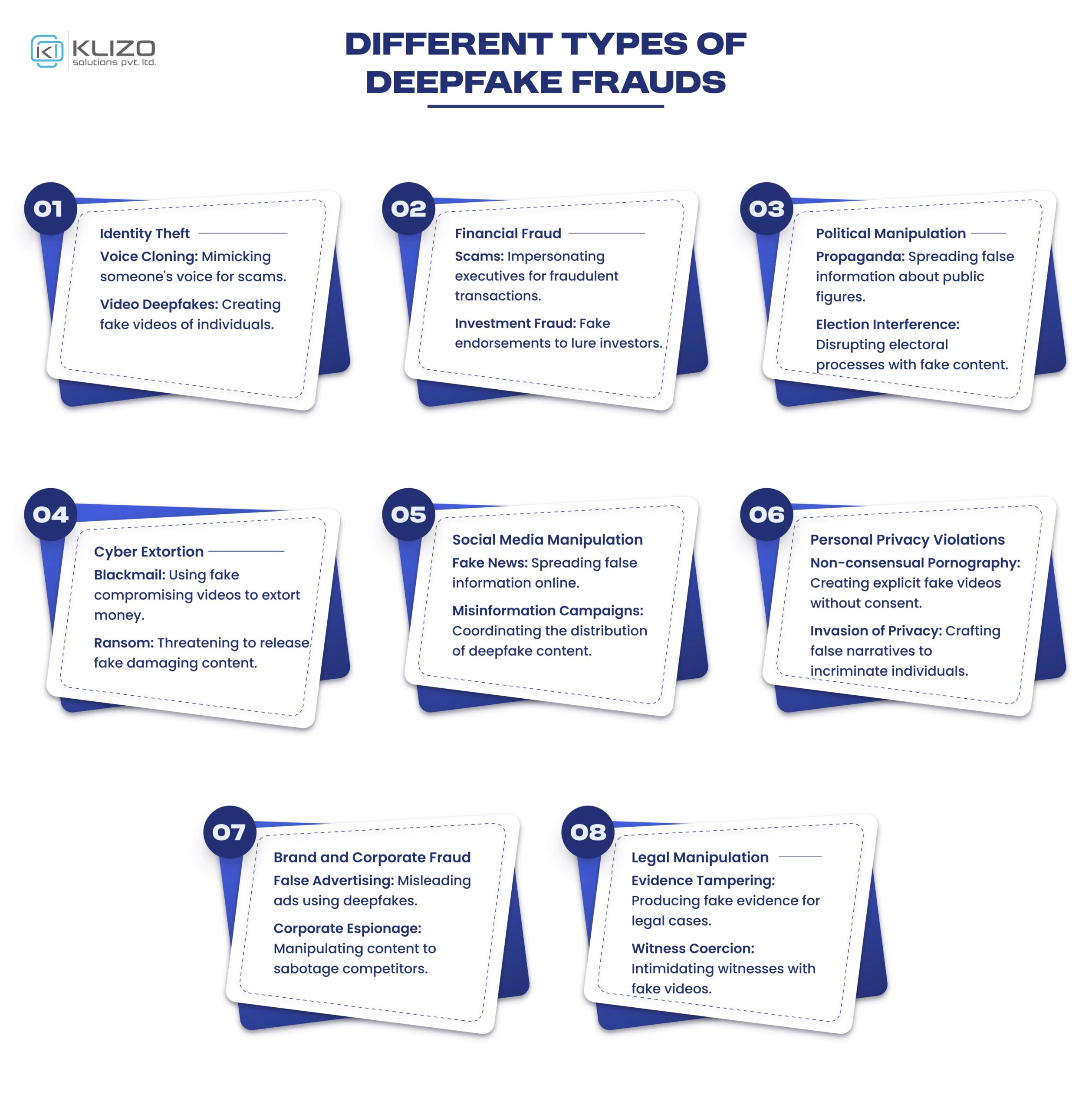
Deepfakes refer to synthetic media—comprising images, videos, and audio—created using artificial intelligence (AI) technology. These creations portray something that does not exist in reality or events that have never occurred.
Essentially, deepfakes use AI to replace the likeness of one person with another in video or audio, blurring the line between truth and deception.
These manipulations can be used for entertainment, such as de-aging actors in movies, or for more malicious purposes, such as spreading misinformation, committing fraud, or damaging reputations.
Deepfake technology leverages artificial intelligence and machine learning to create realistic but fake audio and video content. By using advanced algorithms, deepfakes can manipulate images, videos, or audio to make it appear as if someone is saying or doing something they never did.
Let’s explore the mechanics behind deepfake technology:
The Deepfake technology has the potential for both creative uses in entertainment and harmful applications such as spreading misinformation or committing fraud. Detecting deepfakes often involves analyzing subtle inconsistencies in facial features, lighting, and audio synchronization.
As deepfake technology becomes more sophisticated, the ability to detect and prevent its misuse is critical. Deepfakes can create convincing but false representations of people, leading to misinformation, fraud, and privacy violations.
However, effective detection strategies can help protect individuals and organizations from these risks, ensuring the integrity of digital content and fostering trust in media and communications.
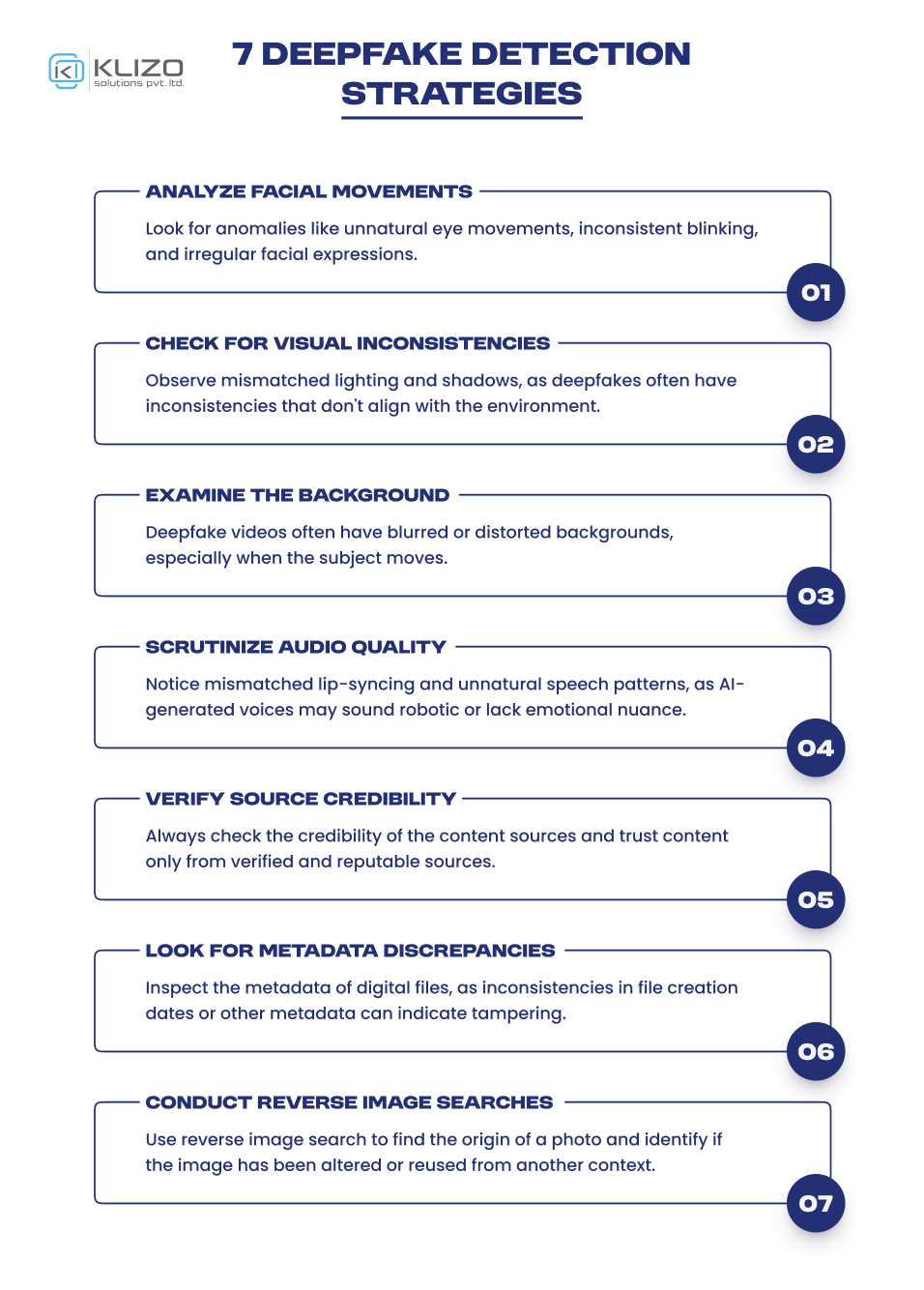
So, without any further delay, let’s delve into the best ways of spotting deepfakes and avoiding deepfake scams:
Examining facial movements is crucial for deepfake detection. AI-generated faces often display unnatural behaviors. So, always pay attention to the following cues:
Example: In early deepfake videos, subjects’ blinking rates were often either too frequent or completely absent, revealing the struggle to replicate natural human behavior.
Identifying mismatched lighting and shadows is another great method of deepfake detection. Since AI-generated images sometimes fail to harmonize the lighting of the inserted face with the background, these inconsistencies can be a tell-tale sign. Here’s how to spot them:
Example: Imagine a video featuring a politician. The shadows on their face appear inconsistent—their left cheek is too bright, while the room lighting suggests otherwise. This discrepancy hints at manipulation.
Backgrounds in deepfake videos are frequently blurred or distorted, especially when the subject is moving. This occurs because the technology often focuses on the face, neglecting the surroundings. So, pay close attention to the video’s surroundings for quick deepfake detection.
Deepfake technology often prioritizes the face, leading to blurred or distorted backgrounds during subject movement.
Example: Imagine a celebrity interview video. As the person moves, the background remains unnaturally static or appears blurred. This discrepancy suggests potential tampering with the video content.
Another effective Deepfake detection technique is looking for mismatched lip-syncing and unnatural speech patterns. Deepfake audio often exhibits the following anomalies:
Example: Imagine a video where a public figure appears to speak, but their lips and voice do not align seamlessly. If the audio seems artificially generated or lacks authenticity, it’s likely a deepfake.
Ensuring the credibility of content sources is a fundamental step in deepfake detection. Trustworthy and verified sources are less likely to distribute manipulated media. Make sure to-
Example: Imagine encountering a video of a celebrity making shocking claims. Before accepting it as genuine, check if reputable news organizations or official social media channels have reported the same information. Their endorsement adds credibility.
As signs of deepfake content, examining the metadata of digital files provides valuable clues. Metadata includes information about file creation, editing, and software used. Here’s what to consider:
Example: Imagine a video claiming to capture a live event. If its metadata reveals that it was created using deepfake software or if the creation date doesn’t match the event timeline, skepticism is warranted. Metadata discrepancies can unmask the deception.
Reverse image searches, a powerful deepfake detection tool, can help trace the origin of a photo or video frame, identifying if it has been altered or reused from another context. This method is effective in spotting content that has been manipulated or falsely attributed. Here’s how they work:
Example: Imagine a suspicious photo of a political figure. A reverse image search reveals that the same image was originally used in a different context—a clear sign of potential deepfake manipulation.
How AI can generate fake content is no longer a secret! Artificial intelligence, particularly through generative models, has become a powerful tool for creating fake content. From deepfakes that manipulate audio and video to AI-generated texts and images, it’s now easier than ever to sow doubt, smear opponents, and influence public debate.
This makes avoiding content misuse more crucial than ever as deepfake detection ensures that creators and businesses retain control over their original work, safeguarding their intellectual property rights. Unauthorized use of content can lead to significant financial losses, so protecting content helps maintain revenue streams derived from licensing, sales, and other monetization methods.
Additionally, AI misuse of content can dilute a brand’s reputation and identity; ensuring proper use of content preserves the brand’s integrity and public perception.
Let’s take a quick look at some of the best ways to avoid content misuse:
Watermarking involves embedding a visible or invisible mark on your digital content, such as images, videos, or documents. This mark can be your logo, brand name, or a unique identifier.
Watermarks serve as a deterrent against unauthorized use. Even if someone attempts to use your content without permission, the watermark is evidence of the original creator.
Many photographers use watermarks on their images before sharing them online. If an image is reused without consent, the watermark helps trace it back to the original owner.
DRM technologies control the use, modification, and distribution of copyrighted content. It includes encryption, access controls, and usage policies.
DRM protects your intellectual property by ensuring that only authorized users can access and use the content in permitted ways. Streaming services like Netflix use DRM to prevent unauthorized copying and distribution of their video content.
Licensing agreements specify how others can use your content. These agreements outline how, where, and for how long the content can be used. Clear licensing agreements provide legal protection and clarify the expectations for content usage, reducing the risk of misuse.
Stock photo websites offer images under specific licenses that define how the images can be used by buyers.
Regularly monitoring where and how your content is being used on the internet helps identify unauthorized usage quickly. Tools like Google Alerts and reverse image searches can assist in this.
For example, authors and artists often use Google Alerts to receive notifications when their work is mentioned online, helping them spot potential misuse. Early detection of content misuse allows you to take timely action, whether legally or by requesting removal.
Informing your audience about the legal and ethical ways to use your content can prevent misuse and help them in avoiding deepfake scams. Also, deepfake awareness and education can promote respect for intellectual property as well as help people spot deepfakes. An informed audience is less likely to misuse content unintentionally.
Deepfake verification tools play a crucial role in safeguarding against the misuse of manipulated content. These tools employ advanced AI algorithms to detect and verify the authenticity of videos and images.
Some of the widely used Deepfake verification tools include Deepware Scanner, Sensity, Reality Defender, FaceForensics++, etc. These AI-powered tools are designed specifically to identify deepfake content in videos and images, helping prevent the spread of manipulated media. Some even utilize blockchain technology to ensure the integrity of videos and images, making it easier to identify tampered content.
When content misuse is detected, legal action or takedown requests can be pursued to have the unauthorized content removed. This can involve sending cease and desist letters or filing DMCA takedown notices.
Legal measures provide a formal way to address and resolve content misuse, ensuring that violators are held accountable. For example, companies frequently use DMCA takedown notices to have infringing content removed from websites and social media platforms.
So you see, by implementing these strategies, you can safeguard your content and maintain control over its rightful use. By prioritizing the prevention of content misuse, you can protect your investments, maintain your competitive edge, and contribute to a respectful and innovative digital landscape.
As we sail through the tempest of digital deception, remember this: skepticism is your life jacket when it comes to deepfake detection.
Deepfakes will persist, but so will our resilience. As discussed above, by staying informed, using deepfake verification tools, critically evaluating suspicious content, and questioning the source, we can keep our heads above water.
Whether you’re an individual trying to protect your digital identity or an organization aiming to safeguard its reputation, understanding and countering deepfakes is essential for deepfake detection and prevention.
So, dear reader, let’s raise your digital magnifying glasses and expose the fakes! Follow Klizo Solutions for more such interesting and informative read on latest trends, technologies, tech threats and more!
Previous article
AI-Driven Optimization: How AI Can Improve Website Performance
Joey Ricard
Klizo Solutions was founded by Joseph Ricard, a serial entrepreneur from America who has spent over ten years working in India, developing innovative tech solutions, building good teams, and admirable processes. And today, he has a team of over 50 super-talented people with him and various high-level technologies developed in multiple frameworks to his credit.

Subscribe to our newsletter to get the latest tech updates.